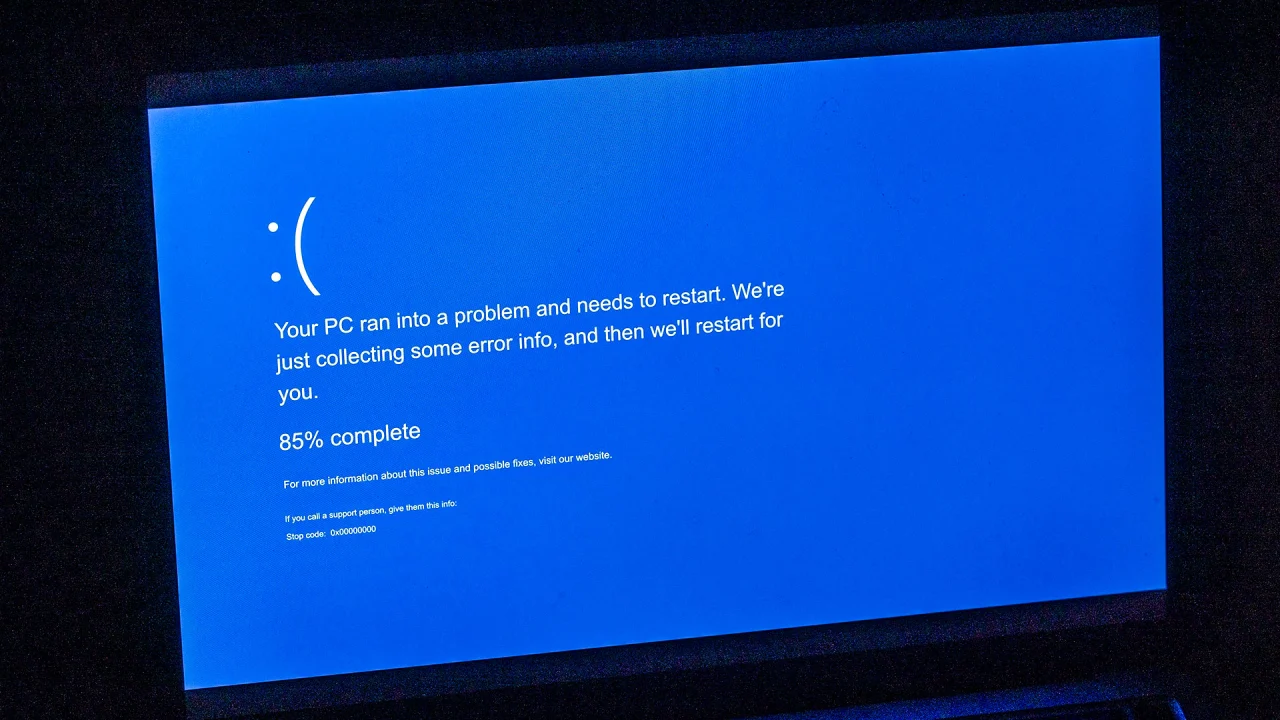
ClickFix fake error message malware spikes over 500%, takes second place as the most abused attack vector
ESET's H2 2025 Threat Report lays bare the new tactics, threats, and trends emerging from the cybercriminal underworld.

- ClickFix is increasingly being used to install infostealers
- The attack vector saw a 500% rise over the past 6 months
- Users are told to run commands in Powershell to fix an error
Use of the ClickFix attack vector has shot up by 517% since the second half of 2024, making it the second most abused attack vector behind phishing.
The attack uses a fake reCAPTCHA to trick users into running code in a Powershell terminal as a ‘fix’ to a fake error.
This causes malware and infostealers to be downloaded and executed on the target device, which then harvest and extract sensitive data back to the hackers.
Infostealers on the rise
ESET’s H2 2025 Threat Report explains how ClickFix is being abused by hackers to distribute some of the most popular infostealing malware, including Lumma Stealer, VidarStealer, StealC, and Danabot.
The attack vector is so effective as it relies on using very simple instructions to trick users into running complex commands in the Powershell terminal. Many users will simply ignore or not understand the commands they are running, instead focusing on trying to fix the error.
ClickFix is usually distributed through phishing emails that will direct the user to a fake website that will require reCAPTCHA verification to access. Powershell commands often bypass antivirus software, making it a particularly effective way to compromise devices especially if the hacker can get the user to do it for them.
In other infostealer news, ESET’s Threat Report shows that SnakeStealer has overtaken Agent Tesla as the most detected infostealer. SnakeStealer was spotted being used in a massive campaign that targeted hundreds of US and EU businesses to steal credentials.
Ransomware gangs experienced an unexpectedly tumultuous period thanks to infighting and rivalries between different ransomware outfits. The DragonForce group launched a spree of defacement campaigns against some of the most infamous ransomware groups including BlackLock, Mamona, and ransomware-as-a-service giant RansomHub.
While there have been significant law enforcement operations against ransomware groups over the past several months, including the 8base seizure, it seems that rivalries have caused the most damage to the ransomware ecosystem.
On the phones front, the recent spate of Kaleidoscope infections have pushed Android adware detections up by 160%. Malware being distributed through official app stores isn’t anything new, with the recent SparkKitty malware being distributed through both the Apple App Store and Google Play Store.
However, the Kaleidoscope malware used a twin-pronged attack method by running intrusive ads on the target device to generate advertising revenue, while also infecting the target devices with a malicious twin app that is downloaded via a third party app store.
“From novel social engineering techniques to sophisticated mobile threats and major infostealer disruptions, the threat landscape in the first half of 2025 was anything but boring,” said Jiří Kropáč ESET Director of Threat Prevention Labs.
You might also like
- Keep your device free from infection with the best antivirus software
- The best password managers will keep your credentials secure
- British man behind ‘IntelBroker’ hacker group charged with stealing millions












![What Is a Markup Language? [+ 7 Examples]](https://static.semrush.com/blog/uploads/media/82/c8/82c85ebca40c95d539cf4b766c9b98f8/markup-language-sm.png)








































![[Weekly funding roundup June 21-27] A sharp rise in VC inflow](https://images.yourstory.com/cs/2/220356402d6d11e9aa979329348d4c3e/Weekly-funding-1741961216560.jpg)