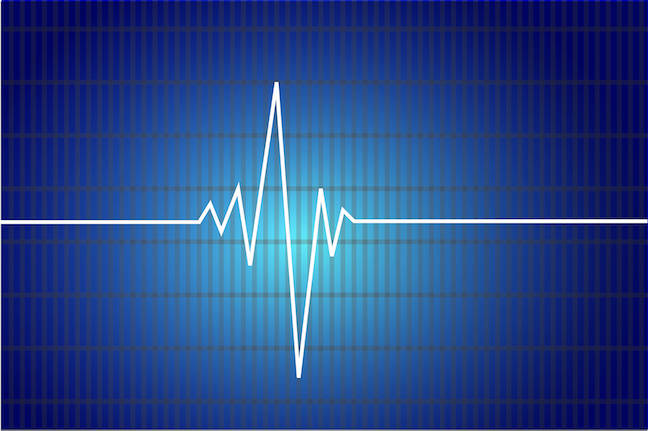
This mega DDoS attack broke all records - huge 37.4TB bombardment in 45 seconds against a single victim is the largest ever recorded
A huge DDoS attack which sent 38TB of data could have wreaked havoc - but it was stopped in its tracks.

- Huge 38TB DDoS attack targeted a hosting provider
- Cloudflare's DDoS protection kicked in and blocked the attack
- This was the largest DDoS attack ever recorded
Distributed-denial-of-service (DDoS) attacks usually use a network of compromised devices to bombard a server with an unusually large amount of data in order to render a service unusable.
But Cloudflare says it recently blocked a monumental DDoS attack which attempted to dump almost 38TB worth of data in just 45 seconds - making it the largest such attack in history.
For comparison, 38TB is the equivalent of downloading 9,350 full-length HD movies, or 9.35 million songs, or 7,480 hours of high-definition video.
Cloudflare blocks mega-DDoS
Cloudflare said the attack resulted in 7.3 terabits per second (Tbps) of traffic hitting an average of 21,925 destination ports on an IP address belonging to an unnamed hosting provider.
The attack used UDP packets as the main attack vector in order to ‘flood’ the IP address with illegitimate packets that the service will be unable to process, making up around 99.996% of the attack.
The remaining 0.004% of the attack used a combination of reflection and amplification attacks which bounce data back onto the victim and amplify the attack, and flood attacks.
Some of the additional attacks used obsolete diagnostic tools to ‘ping’ the IP address for an automatic response, which, when done en masse, overloads the network's ability to respond and amplifies the network’s traffic.
The DDoS attack originated from 161 countries, with just under half of the traffic coming from IP addresses based in Brazil and Vietnam.
Cloudflare said another third of the traffic was traced back to Taiwan, China, Indonesia, Ukraine, Ecuador, Thailand, the United States, and Saudi Arabia.
For the uninitiated, this may make the attack sound like a huge coordinated effort by a highly organized group that span the globe, but in reality the majority of the devices used are compromised internet connected devices that have been infected with malware, turning the device into a ‘bot’.
Hackers will use phishing, malicious downloads, or vulnerabilities to spread the malware, with the infected device continuing to operate as intended until called upon to take part in an attack.
The attack peaked at 45,097 unique source IP addresses per second, with an average of 26,855 for the duration of the attack. To counter the attack, Cloudflare said it used the distributed nature of a DDoS attack to spread the traffic load across data centers close to where the traffic was originating from.
Cloudflare’s DDoS detection and mitigation systems also detect suspicious packets and ‘fingerprints’ them, allowing the system to identify similarities in attack packets and mitigate them without impacting legitimate traffic.
You might also like
- The best antivirus software can keep your devices protected
- Surf the web at speed with the best browser
- DDoS attacks in 2025 have already surpassed the 2024 total





![Is ChatGPT Catching Google on Search Activity? [Infographic]](https://imgproxy.divecdn.com/RMnjJQs1A7VQFmqv9plBlcUp_5Xhm4P_hzsniPsfHiU/g:ce/rs:fit:770:435/Z3M6Ly9kaXZlc2l0ZS1zdG9yYWdlL2RpdmVpbWFnZS9kYWlseV9zZWFyY2hlc19pbmZvZ3JhcGhpYzIucG5n.webp)