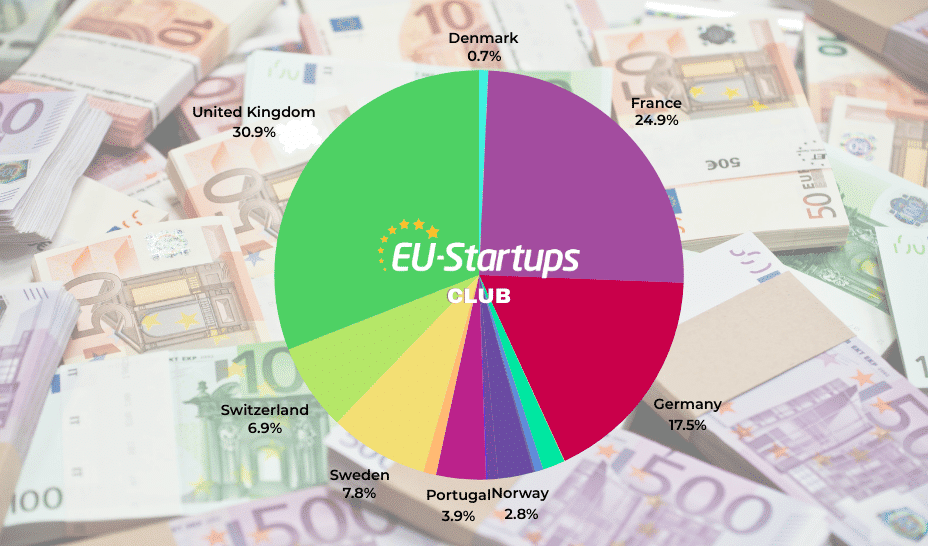
US local governments targeted by Chinese hackers
The Chinese used the Cityworks bug to deploy Cobalt Strike beacons and backdoors.

- Multiple US government agencies were targeted by Chinese hackers, Cisco Talos warns
- The hackers used a bug in Trimble Cityworks
- The vulnerability was fixed in February this year
Local government organizations across the United States were recently targeted by a Chinese threat actor looking to deploy various web shells and malware loaders. This is according to cybersecurity researchers Cisco Talos, who have been tracking the attacks since early 2025.
Cisco says the threat actors are tracked as UAT-6382 (usually short for Unknown Adversary Threat), and have been targeting organizations through a zero-day vulnerability in Trimble Cityworks.
Trimble Cityworks is a Geographic Information System (GIS) asset management and permitting software designed to help local governments and utilities manage infrastructure, maintenance, and operations efficiently.
In February this year, we reported the software was vulnerable to CVE-2025-0994, a high-severity deserialization bug with a severity score of 8.6 (high). The vulnerability allowed threat actors to perform remote code execution (RCE).
Cisco said the attackers used the zero-day to drop a Rust-based malware loader which, in turn, installed Cobalt Strike beacons and VSHell malware, which provided the Chinese with long-term, persistent access.
Patching the flaw
"Talos has found intrusions in enterprise networks of local governing bodies in the United States (U.S.), beginning January 2025 when initial exploitation first took place. Upon gaining access, UAT-6382 expressed a clear interest in pivoting to systems related to utilities management," Cisco said in its security advisory.
With access established, the attackers started dropping different web shells: AntSword, chinatso/Chopper, and more. All of these are written in Chinese. They were also dropping a custom loader called TetraLoader, which was written in Simplified Chinese.
As soon as news of the zero-day broke, Trimble released a patch, bringing Cityworks to versions 15.8.9 and 23.10 and mitigating the risk. It also warned about discovering some on-prem deployments having overprivileged IIS identity permissions, and added that some deployments haid incorrect attachment directory configurations.
At the time, there were no reports of victims or damages, but the US Cybersecurity and Infrastructure Agency (CISA) still released a coordinated advisory, urging customers to apply the patches as soon as possible. In early February, the agency added it to KEV, giving Federal Civilian Executive Branch agencies a deadline to patch.
Via BleepingComputer
You might also like
- Hackers are hijacking government software to access sensitive servers
- We've rounded up the best password managers
- Take a look at our guide to the best authenticator app











.png)





































![[Weekly funding roundup May 17-23] VC inflow remains steady](https://images.yourstory.com/cs/2/220356402d6d11e9aa979329348d4c3e/Weekly-funding-1741961216560.jpg)